Intelligent Integrated Security Solution
Algorithm-based threat analysis method
Identify invisible threat information
-
01
Log/Network Collection
- >
-
02
Big data storage
- >
-
03
Analyze threat information
- >
-
04
Customizing


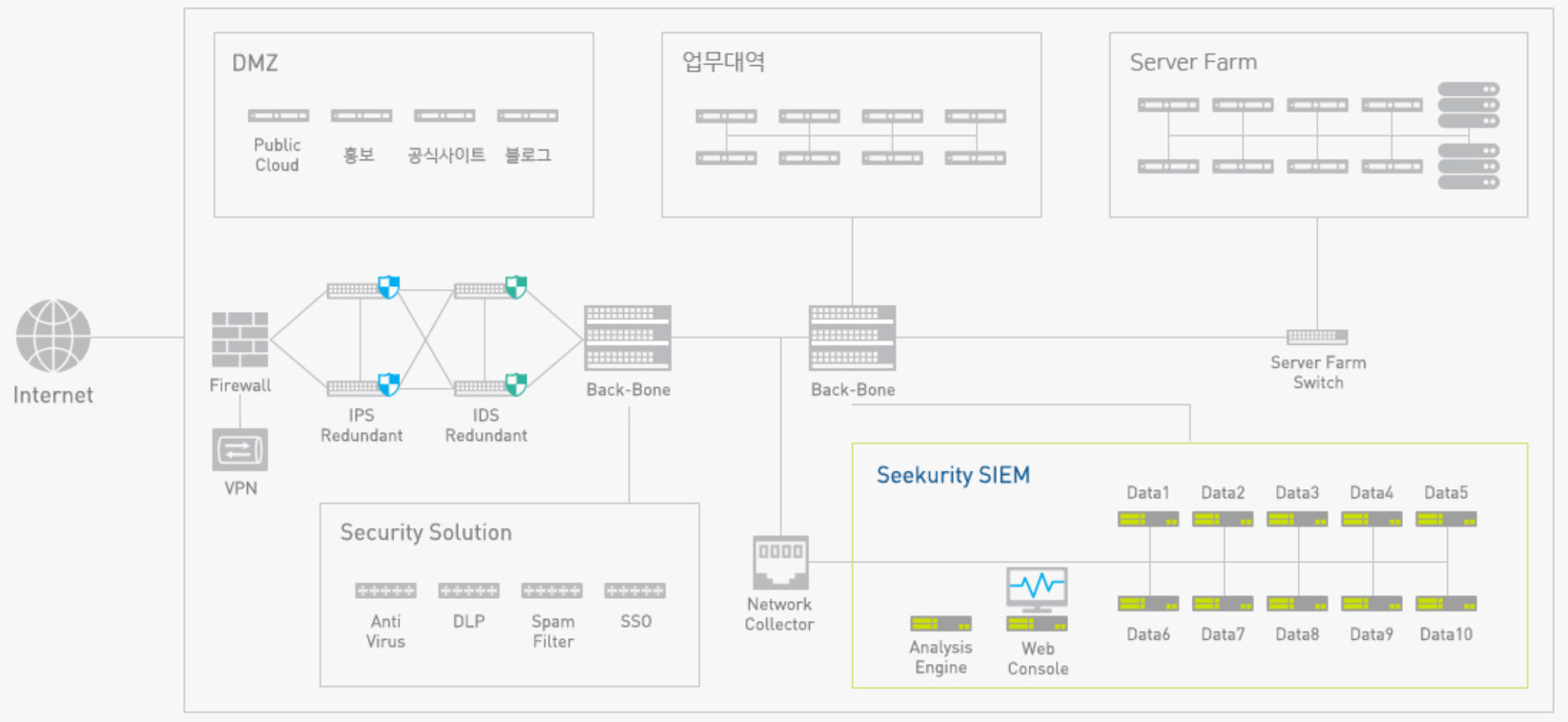
Seekurity SIEM Configuration
Internet boundary section, internal network, system, EndPoint, etc.
Integrated automation-based control based on integrated infrastructure system.
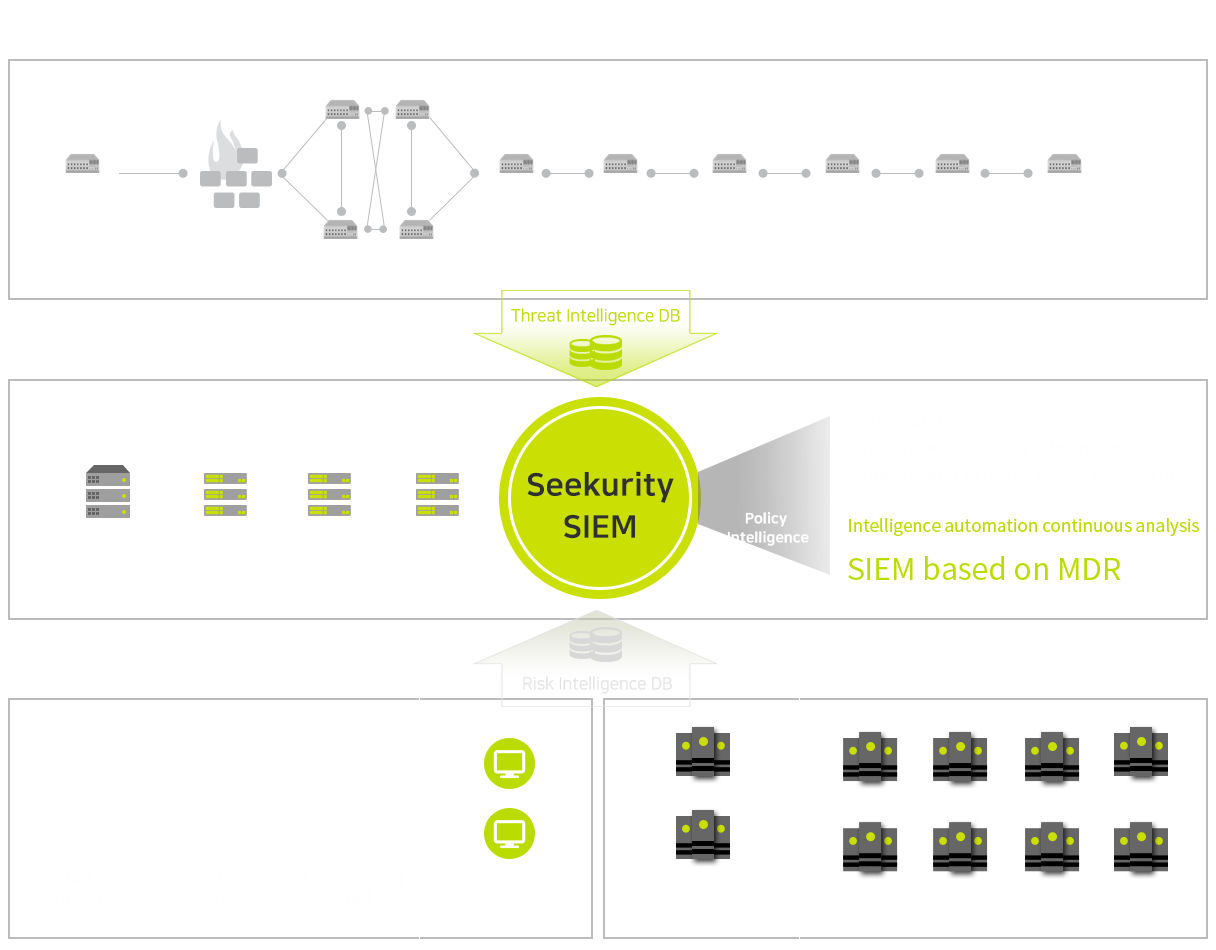
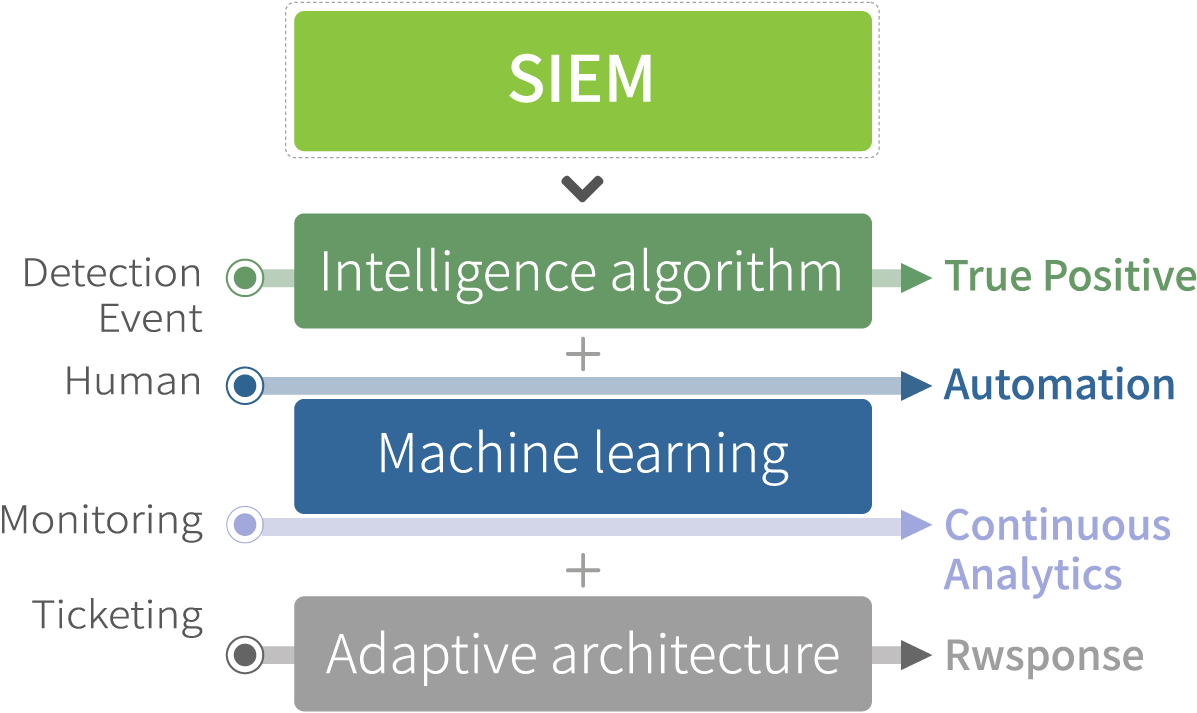
Features of using MDR based SIEM (Managed Detection and Response SIEM)
MDR based SIEM

Algorithm
From Human-based passive control
To System-based Automatic Control
Intelligence
From numerous event control
From numerous event control
Machine learning
Based on the major events
Based on the major events
Seekurity SIEM expected effect
Robust automation-based integrated security environment configuration and TCO reduction with clear purpose
(SIEM, Threat DB, Vulnerability Scanner, NVD DB, SPAN traffic collection)


Seekurity SIEM brochure
Seekers brochures are available for download.





 02.2039.8160
02.2039.8160 02.2039.8161
02.2039.8161 contact@seekerslab.com
contact@seekerslab.com